Two Factor Authentication
Users can have increased protection for their accounts through two-factor Authentication method. This helps users keep their accounts secure as the system asks for a ‘One Time Pin’ (OTP) after the user logs in with their credentials.
OTP can be sent to either user’s email account or phone number based on the availability of either-or choice of the user.
If two-factor authentication is enabled for a user, based on user’s data, Email, Phone Number, or both can be used to receive OTP.
The following screen is displayed as the user logs in with their credentials.
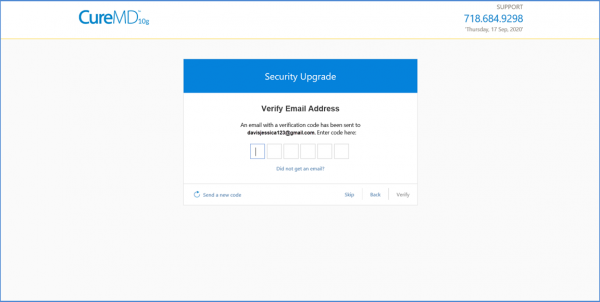
If the user enters a wrong code, the system shows an error and allows a retry.
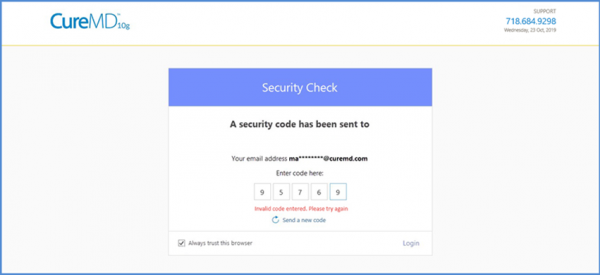
Please contact Support Team to learn more or have it enabled for your user.
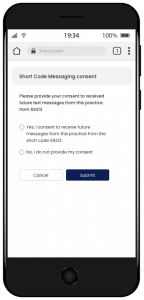
With this enhancement in the CureMD application, OTP messages for two-factor authentication are going to be sent via short codes.
Users receive an SMS containing a short URL that directs them to a consent form.
However, if the user tries to tap the link again or use an old link, the system shows them a message that says “Your response has already been submitted.” This means that they have already filled out the form and agreed to receive messages via the short code.
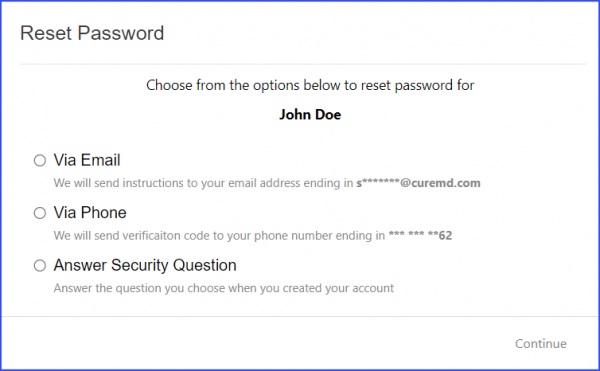
The users can get their password recovered by clicking on the ‘Forgot Password’ link on CureMD application’s login page after which three options are displayed to reset the password.
Users who have their phone numbers linked to their profile; an immediate One-Time Password (OTP) is dispatched to their number. This OTP is a temporary code that helps verify the user’s identity.
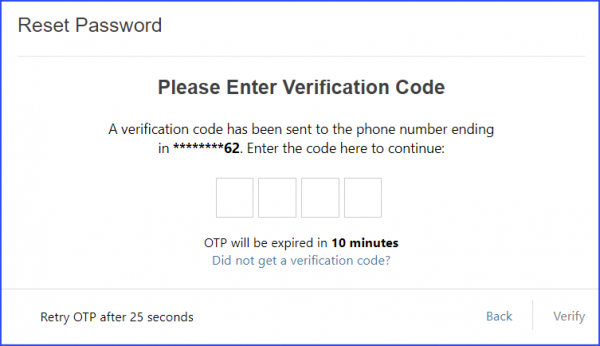
When entering the OTP on the website/app, the user sees a reminder that the OTP is valid for only 10 minutes. This means they have a window of 10 minutes from the time of receipt to use this code. If the user enters the OTP within its 10-minute validity, they’re taken straight to a screen where they can set a new password. If they miss that window and try to use the OTP after it’s expired, the system does not allow it and suggests that they start the OTP process from the beginning.
The system has built-in protections to prevent malicious activities. Once the OTP is dispatched to the user, they can’t immediately ask for another one. The option to request a send a new code is temporarily paused for 25 seconds. After this brief wait, they can ask for a new OTP if needed.
To reinforce the security of user accounts, the number of OTP attempts a user can make have been restricted.
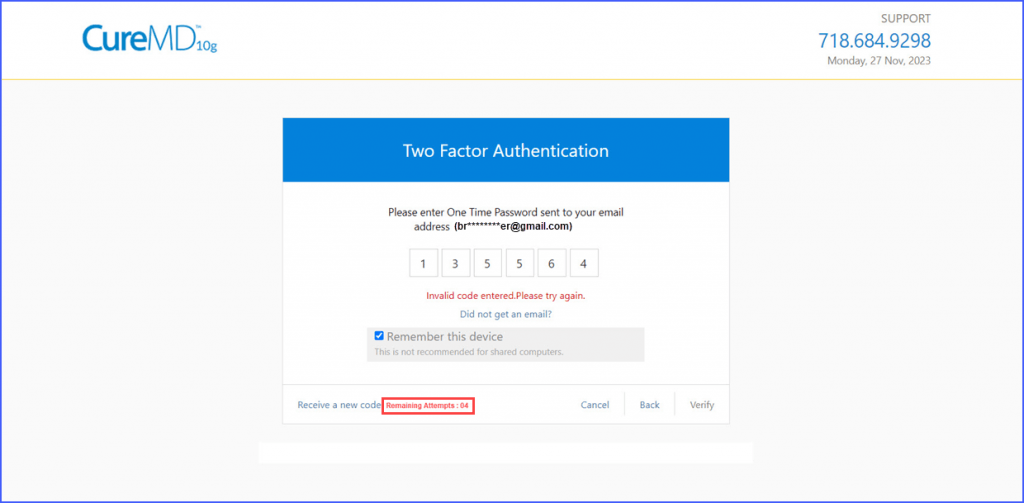
When a user attempts to log in using 2FA and requests an OTP, the system allows a maximum of five requests. This limit is cumulative across both phone and email OTP methods. The first count is initiated upon starting the 2FA process but is not deducted from the total of five. The system displays the remaining number of OTP attempts available to the user.
If the user enters the correct OTP and is successfully able to log in, the OTP counter resets.
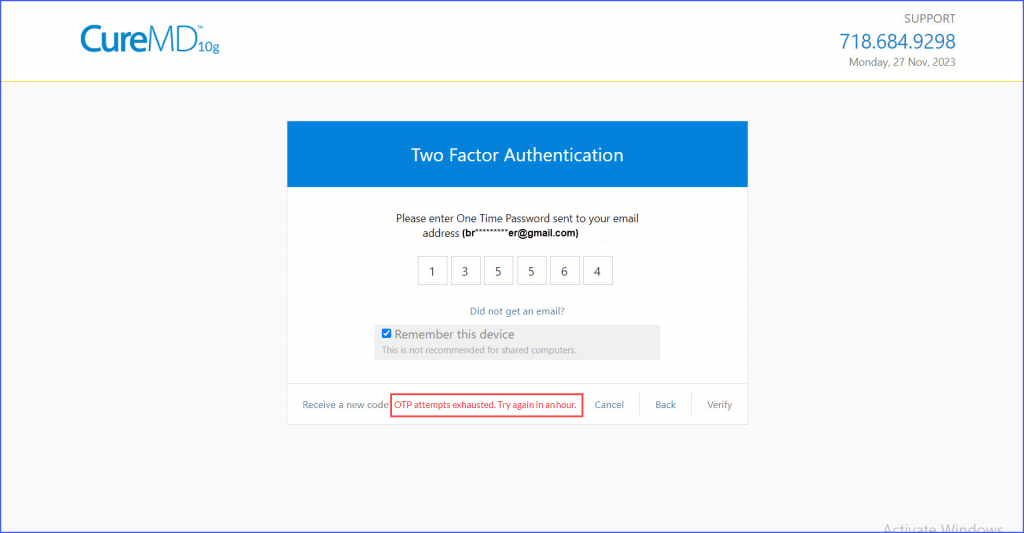
However, if a user fails to enter the correct OTP in five attempts, any further request to generate an OTP results in the account being locked for one hour. A message, “OTP attempts exhausted. New code available in an hour,” is displayed, replacing the OTP counter. Additionally, the ‘Receive a new code’ button is subsequently disabled.
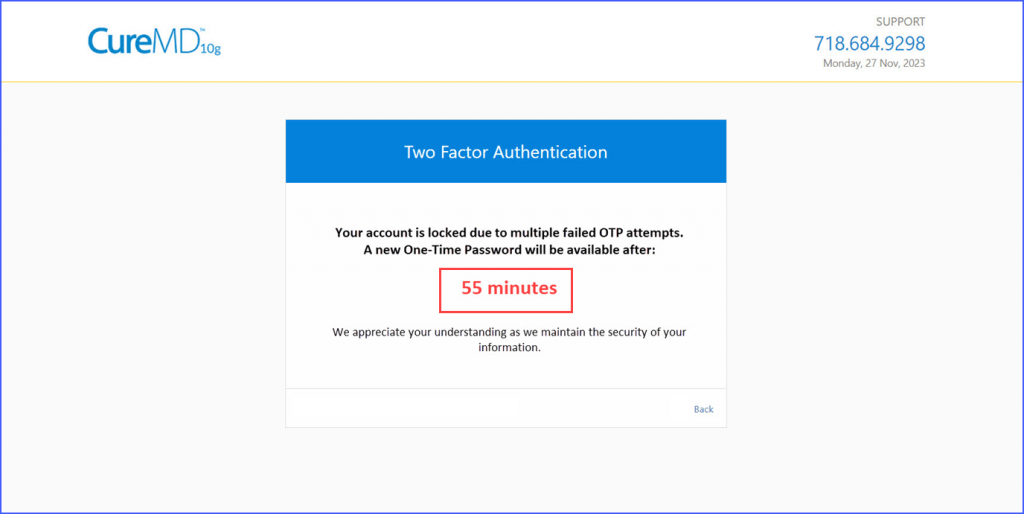
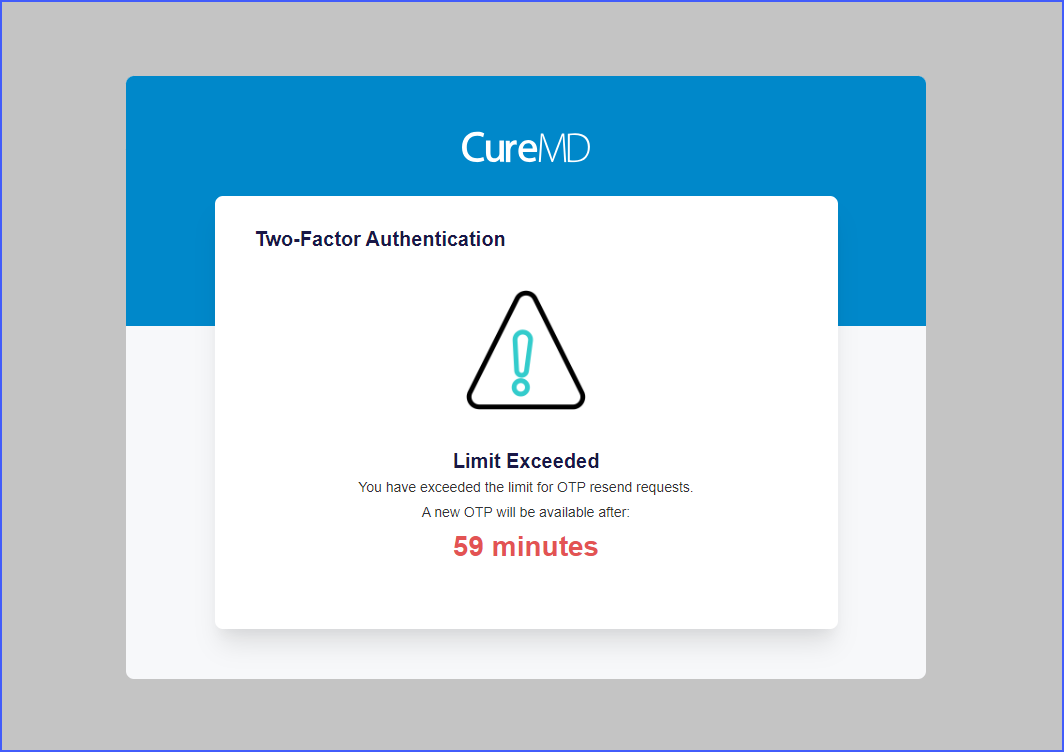
Moreover, if the wait time of one hour for requesting a new OTP has not elapsed, and the user tries to log in again, they encounter an “OTP Request Limit Reached” screen with a real-time timer, indicating the remaining wait time before the next login attempt is possible.
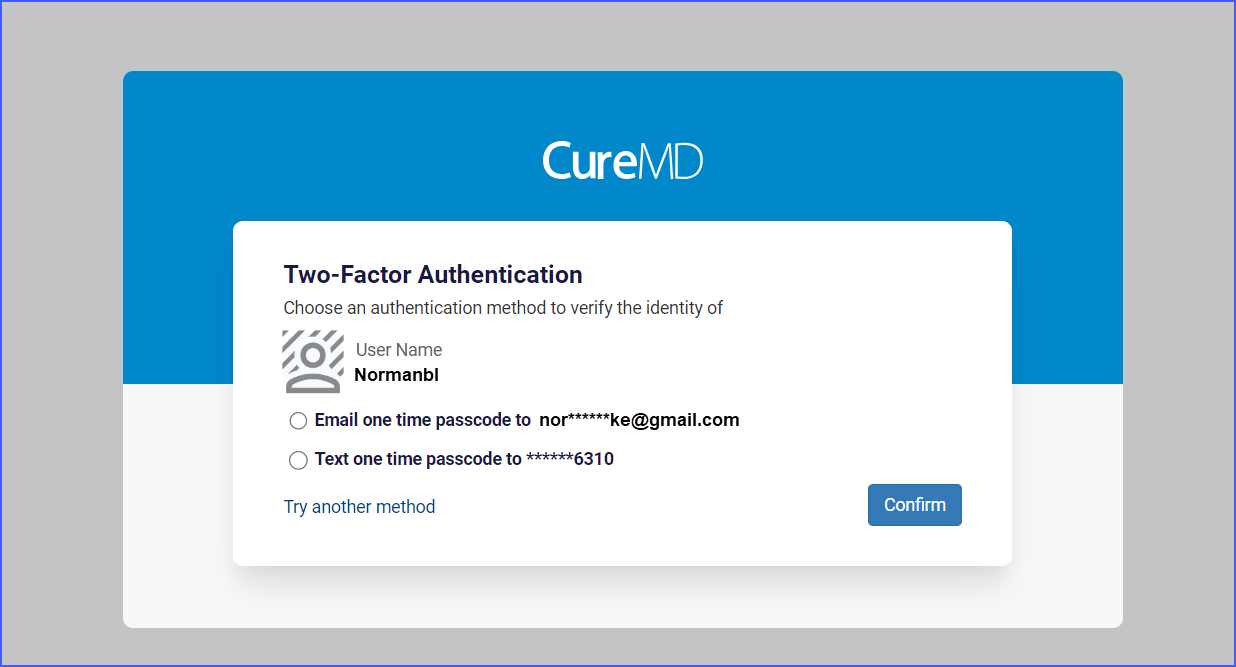
Upon logging in, if the user has both email and phone numbers verified, the system presents options to receive an OTP via either method. ![]()
The user selects their preferred method and clicks ‘Confirm’ to proceed to the OTP entry page. If only one verification method is available, the user sees only that option for OTP delivery.
On the OTP entry page, users can add their device to a trusted list, allowing them to bypass 2FA on that device for 45 days.
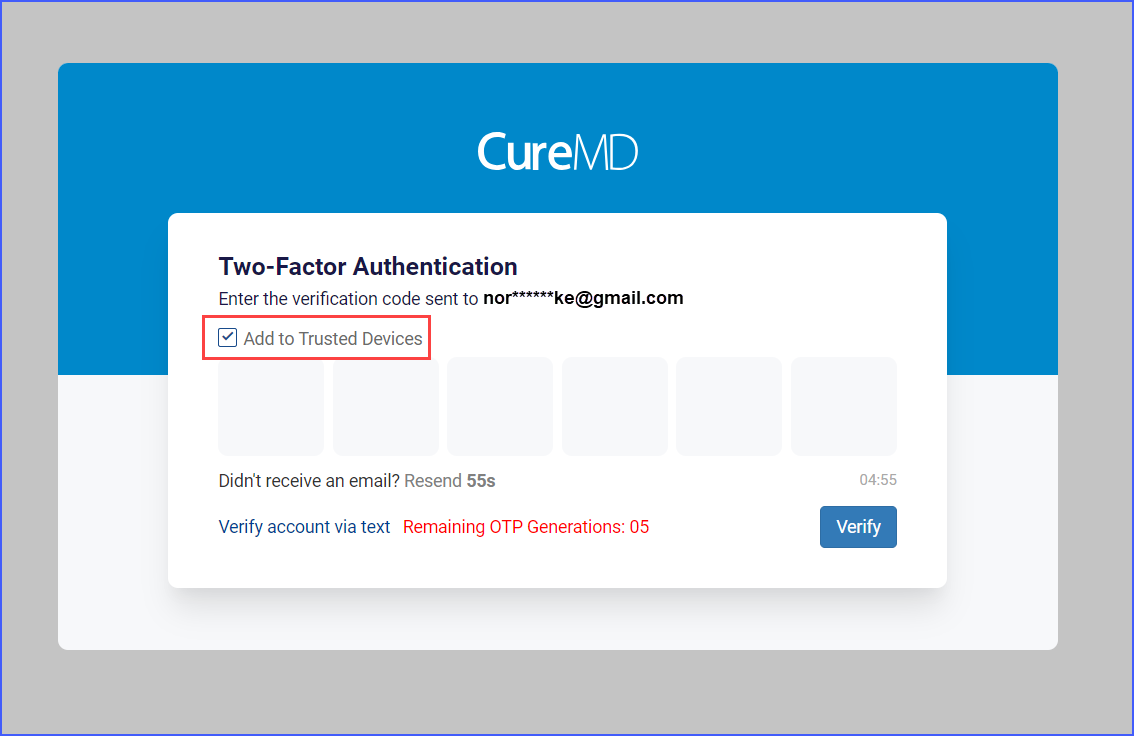
As previously done, if the user does not receive the OTP within one minute, they have the option to request a resend up to five times, with a one-minute waiting period between each request.
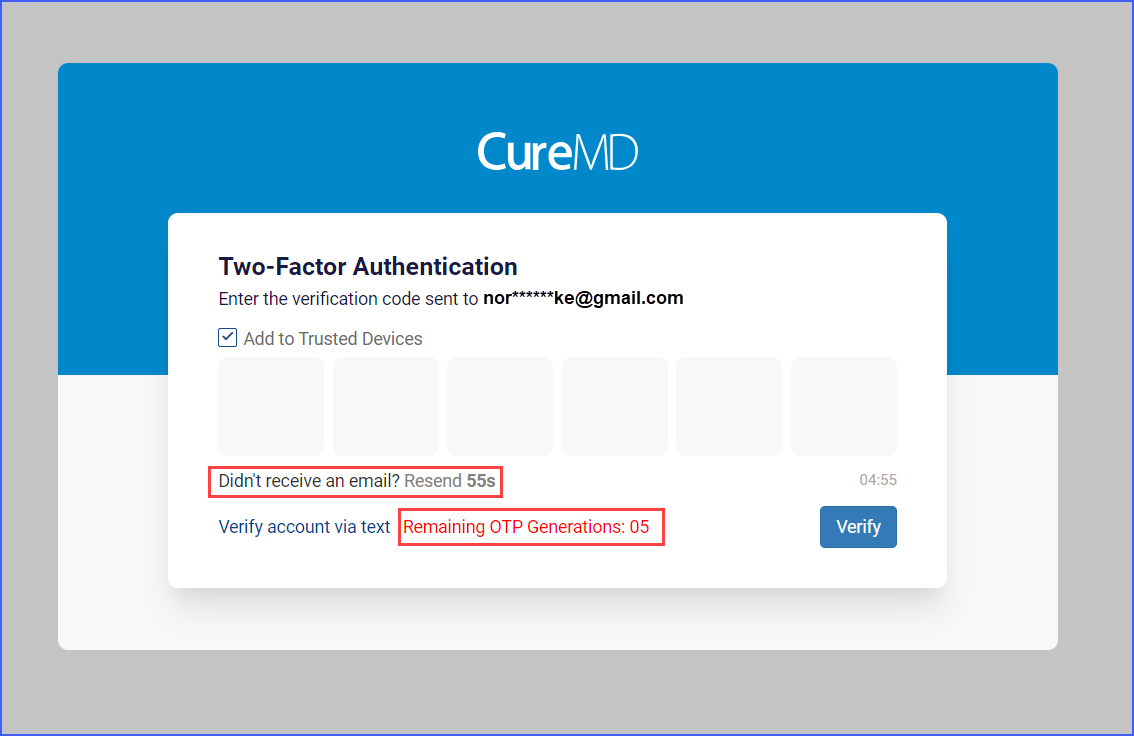
In cases where the OTP is not received, a “Resend” option becomes available after one minute, invalidating the previous OTP and generating a new one. Users are restricted to five resend requests before being prompted to contact support.
OTPs are valid for five minutes, after which an error message prompts user to generate a new one.
Once verification is completed successfully, a confirmation screen appears. However, after five incorrect attempts, users must regenerate the OTP code to proceed further. New OTPs can be generated up to 5 times, after which a 1-hour lockout time is initiated.
If users opt to switch their verification method from email to phone, the original OTP sent to email is invalidated, a new OTP is dispatched to the phone, and the user is redirected to enter the new OTP.
